Collect Sysmon Logs with Windows Event Source
Example configuration steps for capturing Sysmon logs using the Windows Event source.
Prerequisites
About Sysmon logging
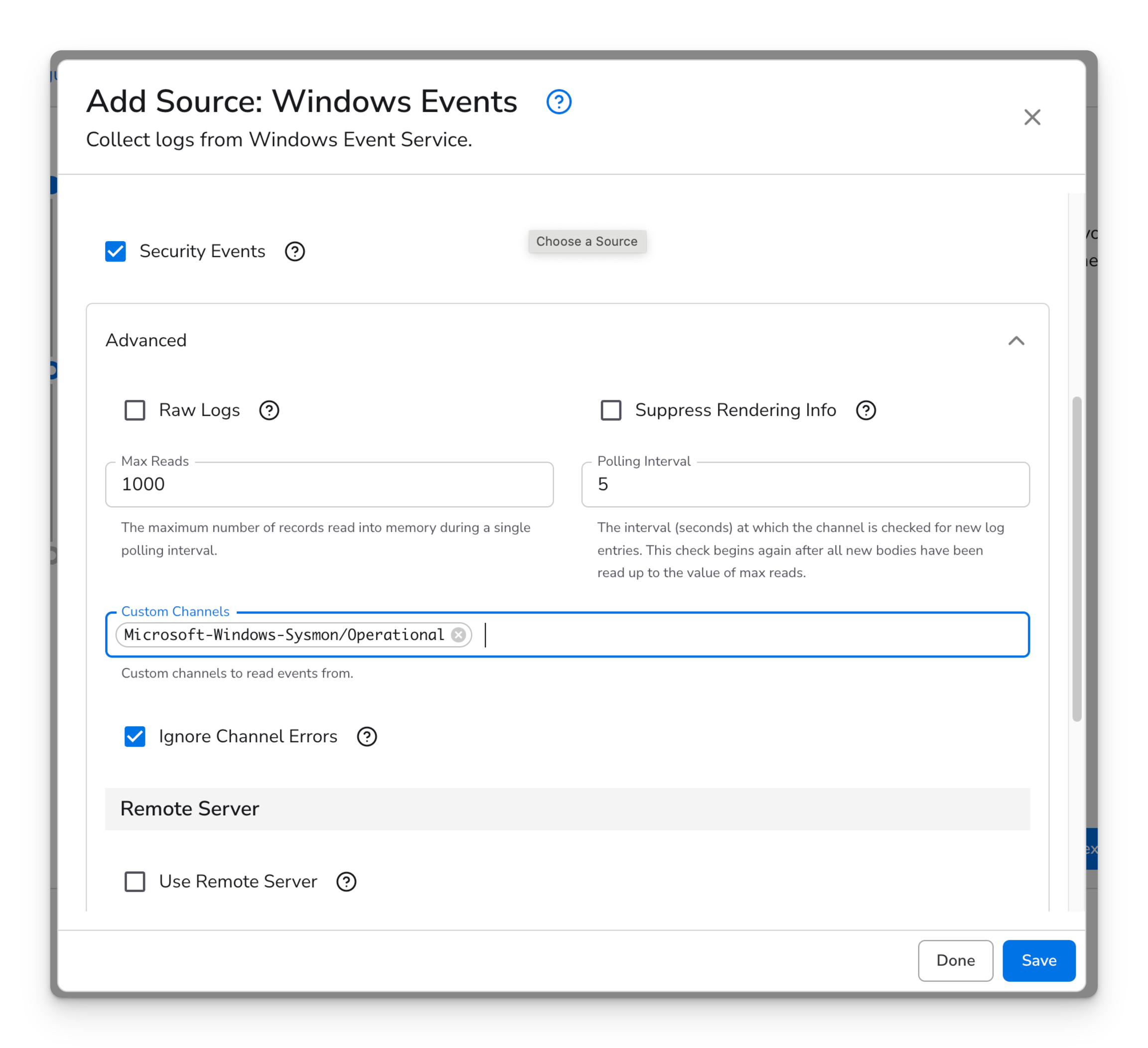
Microsoft-Windows-Sysmon/OperationalSteps
Microsoft-Windows-Sysmon/Operational
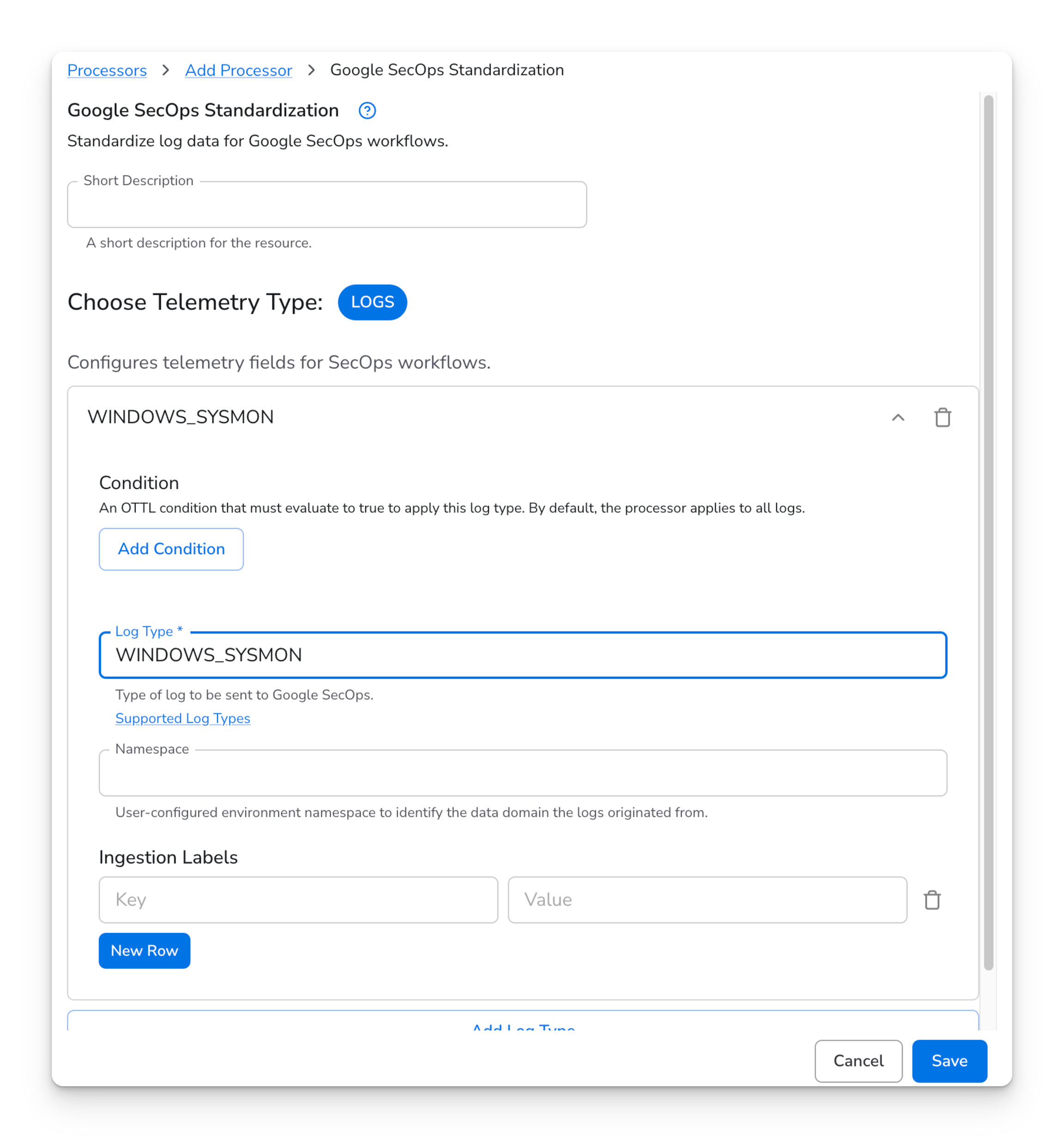
Sending Sysmon logs to Google SecOps
Troubleshooting
Was this helpful?